
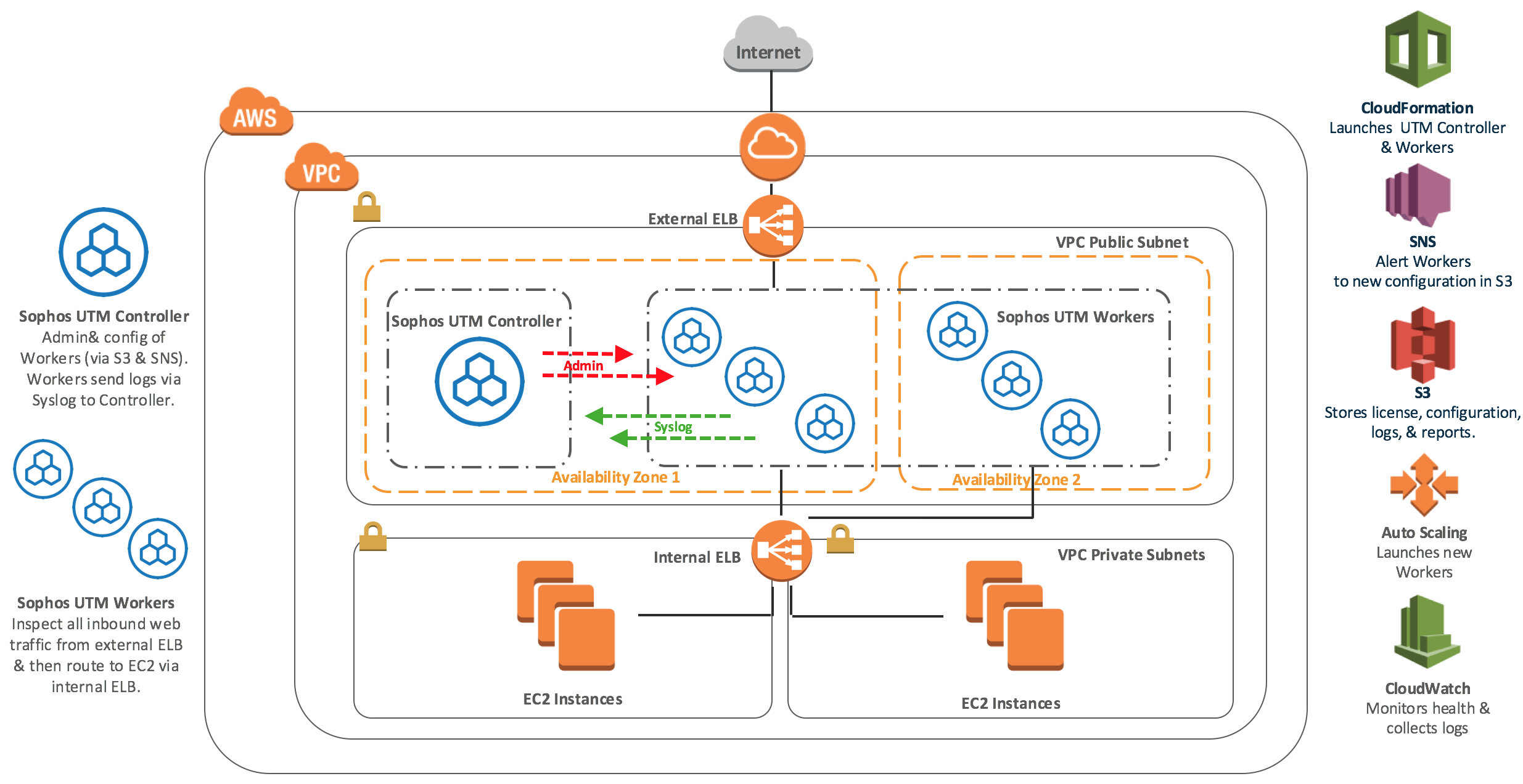
Checking the Sophos XG Web Server Protection Logs. In the Sophos XG management console click Log Viewer in the top right. Select Web server protection on the right-hand drop down box and you should see an entries similar to the image below. With support for Server Name Indication (SNI), web server protection will present the correct server to each client, based on the requested hostname. Go to Firewall and select IPv4 using the filter switch. Click + Add firewall rule and Business application rule. Enter the general rule details. The Sophos XG 450 firewall is one of the best enterprise firewalls that offers superior performance with a simple management interface. These XG 450 firewalls are rated for 751-1000 users, 50 Gbps firewall throughput, and 5.5 Gbps VPN throughput. Web Server Protection. Includes Web Application Firewall to protect against a variety of web. This demonstration walks through the process of configuring Advanced Threat Protection on the Sophos XG Firewall. Configure SF-OS to use LDAP Server for Authentication. This video helps you understand how to create and manage web protection rules, in order to control the content users are able to access over the web. Sophos XG Webserver Protection Licenses, Subscriptions & Renewals Unleash the full potential of your network All XG Webserver Protection Licenses, Subscriptions & Renewals can be found on their own individual product pages or purchase them below, more options can be found on individual product pages. Can't find the part you are looking for?
WAF rules allow you to control the HTTP traffic of a web application over the IPv4 protocol.


Sophos Xg Home
You can configure more than one WAF rule on a given network interface or port, using different hostnames and certificates. With support for Server Name Indication (SNI), web server protection will present the correct server to each client, based on the requested hostname.
- Go to Firewall and select IPv4 using the filter switch.
- Click + Add firewall rule and Business application rule.
- Enter the general rule details.
Application template
Select Web server protection (WAF) to define an application filter policy for HTTP based applications.
Rule name
Enter a name for the rule.
Description
Enter a description for the rule.
Rule position
Specify the position of the rule.
Rule group
Specify the rule group to add the firewall rule to. You can also create a new rule group by using Create new from the list.
If you select Automatic, the firewall rule will be added to an existing group based on first match with rule type and source-destination zones.
- Enter Hosted server details.
Hosted address
Select the interface of the hosted server to which the rule applies. It is the public IP address through which internet users access the internal server/host.
When a client establishes a connection and accesses the web server, the web server does not obtain the client’s real IP address. The server obtains the address of the interface used by the web application firewall (WAF) because the connection is made through the WAF. The client’s real IP address is available in the HTTP header
Listening port Enter a port number on which the hosted web server can be reached externally over the internet. Default is port 80 for plaintext communication (HTTP) and port 443 for encrypted communication (HTTPS).
HTTPS
Select to enable or disable scanning of HTTPS traffic.
HTTPS certificate Only with HTTPS.
Select the HTTPS certificate to be used.
Redirect HTTP Only with HTTPS.
Select to redirect HTTP requests.
Domains
HTTPS disabled: Enter the FQDN configured on the web server, for example, shop.example.com.
HTTPS enabled: Depending on the HTTPS certificate you select, some domains may be preselected. You can edit or delete these domains or add new ones.
- Specify Protected server(s) details.Path-specific routing
You can enable path-specific routing to define (a path) to which web servers incoming requests are forwarded.
You can define that all URLs with a specific path, for example, /products/, are sent to a specific web server. On the other hand you can allow more than one web server for a specific request but add rules how to distribute the requests among the servers. Additionally, you can define that each session is bound to one web server throughout its lifetime (sticky session). This may be necessary if you host an online shop and want to make sure that a user sticks to one server during the shopping session. You can also configure to send all requests to one web server and use the others only as a backup.
For each hosted web server, one default site path route (with path /) is created automatically. The device automatically applies the site path routes in the most reasonable way: starting with the strictest, that is, longest paths and ending with the default path route which is only used if no other more specific site path route matches the incoming request. The order of the site path route list is not relevant. If no route matches an incoming request, (in case the default route was deleted), the request will be denied.
Add new path
(Only available if Path-specific routing is selected. Only active after at least one web server and one hosted web server have been created.) Click Add path to define a new path.
Web server
(Not available if Path-specific routing is selected.)
With this option, you select the web servers that are to be protected. Select a web server from Web server list. The selected web server is displayed on the right side of the table under Selected web server(s).
A new web server can be created on the Web server > Web servers page.
- Specify Access permission details. (Not available if Path-specific routing is selected.)Allowed client networks
Select or add the allowed networks that should be able to connect to the hosted web server.
Blocked client networks Select or add the denied networks that should be blocked to your hosted web server.
Authentication
Select a web app authentication profile or click Create new to create a new authentication profile.
- Add path Exceptions for the web servers.
Click Add new exception to specify a new exception.
- Specify policies for business applications in the Advanced section.
Protection
Select an application protection policy for the server or create a new one.
Intrusion prevention
Select an intrusion prevention policy for the rule or create a new one.
Traffic shaping
The traffic shaping policy allocates and limits the maximum bandwidth usage of the user.
- Specify additional options for the added server in the Advanced section.
Disable compression support
By default, this check box is disabled and the content is sent compressed when the client requests compressed data. Compression increases transmission speed and reduces page load time. However, if websites are displayed incorrectly or users experience content-encoding errors when accessing your web servers, it may be necessary to disable compression. When the check box is enabled, the WAF will request uncompressed data from the web servers of this hosted web server and will send it uncompressed to the client, independent of the HTTP request’s encoding parameter.
Rewrite HTML
Select this option to have the device rewrite links of the returned web pages in order for the links to stay valid. Example: One of your web server instances has the hostname yourcompany.local but the hosted web server’s hostname on the device is yourcompany.com. Thus, absolute links like [a href='http://yourcompany.local/'] will be broken if the link is not rewritten to [a href='http://yourcompany.com/'] before delivery to the client. However, you do not need to enable this option if either yourcompany.com is configured on your web server or if internal links on your web pages are always realized as relative links. It is recommended to use the option with Microsoft’s Outlook web access and/or SharePoint portal server.
HTML rewriting affects all files with a HTTP content type of text/* or *xml*, where * is a wildcard. Make sure that other file types, for example, binary files, have the correct HTTP content type, otherwise they may get corrupted by the HTML rewriting process.
Rewrite cookies
Select this option to have the device rewrite cookies of the returned web pages.
Pass host header
When you select this option, the host header as requested by the client will be preserved and forwarded along with the web request to the web server. Whether passing the host header is necessary in your environment depends on the configuration of your web server.
- Click Save.As soon as a new HTTP-based rule configuration has been created and saved or an existing HTTP-based rule configuration has been altered and saved, all HTTP-based business rules will be restarted. Any underlying client connection using a HTTP-based business rule will get lost and has to be re-established.
Web Server Protection Sophos Xg
