The most widely used password managers sport fundamental vulnerabilities that could allow malware to steal the master password or other passwords stored by the software directly from the computer’s memory, researchers with Independent Security Evaluators (ISE) have found.
- Jeffrey Goldberg 1password Youtube
- Jeffrey Goldberg 1password Facebook
- Jeffrey Goldberg 1password -
- Jeffrey Goldberg 1password Wikipedia
The findings
They tested the 1Password, Dashlane, KeePass and LastPass password manager applications for Windows, which are collectively used by 60 million users and 93,000 businesses worldwide.
They reverse engineered each software package to evaluate its handling of secrets in its various states: not running, running and unlocked, running and locked.
- “Attackers don’t go and blindly try all eight letter passwords and all nine letter passwords,” Jeffrey Goldberg, security guru for the 1Password password manager, told Gizmodo.
- “Attackers don’t go and blindly try all eight letter passwords and all nine letter passwords,” Jeffrey Goldberg, security guru for the 1Password password manager, told Gizmodo.
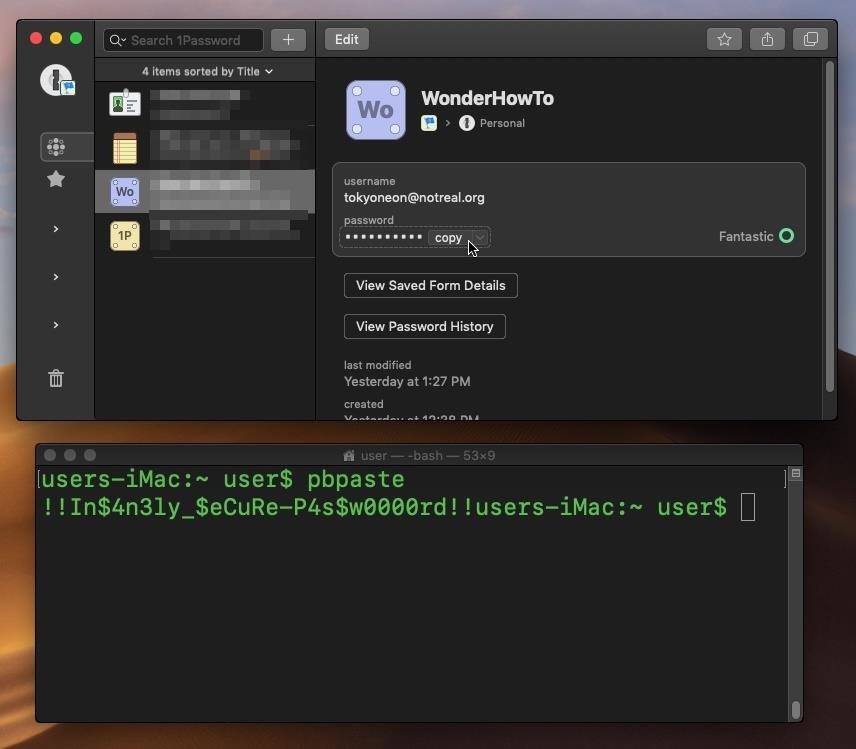
- Avoiding the clipboard with 1Password and Lollipop by Jeffrey Goldberg on Nov 22, 2014 Copy & Paste clipboards (or “pasteboards” as they are called on Mac and iOS) can be dangerous places for secrets if you have malicious software running on your device.
- Jeffrey Goldberg Chief Defender Against the Dark Arts at 1Password. Nerd who does not know how to present himself in a business-like way.
Jeffrey Goldberg Chief Defender Against the Dark Arts at 1Password. Nerd who does not know how to present himself in a business-like way. Adobe premiere elements templates download. Plano, Texas 268 connections.
“We expected and found that all password managers reviewed sufficiently protect the master password and individual passwords while they are not running,” they noted. “We expected and found that all password managers reviewed sufficiently protect the master password and individual passwords while they are notrunning.”
But they found that standard memory forensics can be used to extract the master password and other passwords/secrets these applications are supposed to guard when in the “running and locked” state.

“Keylogging and Clipboard sniffing are known risks and only included for user awareness, that no matter how closely a password manager may adhere to our proposed ‘Security Guarantees’, victims of keylogging or clipboard sniffing malware/methods have no protection,” the researchers noted.
“However, significant violations of our proposed security guarantees are highlighted in red. In an unlocked state, all or a majority of secret records should not be extracted into memory. Only a single one, being actively viewed, should be extracted. Also, in an unlocked state, the master password should not be present in either an encrypted or obfuscated form.”
Unfortunately, all the tested managers failed in at least one aspect of the protection they should provide.
The researchers urge the developers of password managers to sanitize secrets when a password manager is placed into a locked state, but also to employ methods to thwart software based keyloggers and prevent secrets exposure in an unlocked state, to employ trivial malware and runtime process modification detection mechanisms, and more.

Users are not advised to stop using password managers, but to shut them down completely when not in use and to use full disk encryption to prevent the possibility of secrets extraction in the event of crash logs and associated memory dumps. Adding 1password to chrome.
Comments from the software developers
LastPass CTO Sandor Palfy says they’ve already implemented changes to LastPass for Applications designed to mitigate and minimize the risk of the potential attack detailed in the report.
“To mitigate risk of compromise while LastPass for Applications is in a locked state, LastPass for Applications will now shut down the application when the user logs out, clearing the memory and not leaving anything behind,” he told Help Net Security.
Jeffrey Goldberg, 1Password‘s Chief Defender Against the Dark Arts, says that the issues reported by the researcher are well known, but that any plausible cure may be worse than the disease.
“Fixing this particular problem introduces new, greater security risks, and so we have chosen to stick with the security afforded by high-level memory management, even if it means that we cannot clear memory instantly. Long term, we may not need to make such a tradeoff. But given the tools and technologies at our disposal, we have had to make a decision as to how best to keep our users secure. I stand by our decision,” he noted.

He also pointed out that the realistic threat from this issue is limited. “An attacker who is in a position to exploit this information in memory is already in a very powerful position. No password manager (or anything else) can promise to run securely on a compromised computer.”
Dashlane CEO Emmanuel Schalit pointed out that in the scenario discussed an attacker has total control of a user’s device, which meas that he can read any and every information on the device.
“In such a case, the attacker can also see everything that is typed by the user including passwords and credit card numbers, any information being exchanged by the device over the internet even if it is sent over https, any information the device is able to capture (audio, video, etc.) through the hardware attached to it, regardless of whether the user employs a password manager or not,” he explained.
“For that reason, it is generally well known in the world of cybersecurity that the above scenario is an extreme one, in the sense that no mechanism can protect the digital information on a device if that device is already entirely compromised. Please note that this does not apply to the data Dashlane stores on your device. The data stored by Dashlane on the device (i.e. on the hard drive) is encrypted and cannot be read by an attacker even if the attacker has full control of the device. This only applies to the data present in the memory of the device when Dashlane is being used by a user who has typed the Master Password.”
No solution is 100 percent perfect and users should not stop using password managers as they protect against the most common threat (reusing of potentially compromised passwords). In comparison, an attacker being able to specifically take control of the device of a single user is a much less likely threat, Schalit noted.
Jeffrey Goldberg 1password Youtube
“At the end of the day the only real protection against a scenario where an attacker has fully compromised a device is to not use that device. It is for that reason that most (if not all) reputable security experts recommend the use of password managers, while they are fully aware of the above scenario,” he concluded.
Category: «Did you know that..?», «Software», «Tips & Tricks»
41 2 - 43
We received some great feedback on the original article about attacking master passwords of several popular password managers. In one discussion, our benchmark numbers for 1Password were questioned. We had no choice but to re-run the benchmarks and publish an updated chart along with some technical details and explanations. We bring our apologies to AgileBits, the developers of 1Password, for letting the wrong number creep in to our benchmark. Can we still break into 1Password by attacking the master password? Please bear with us for up-to-date information and detailed technical discussion.
We must make one thing extremely clear: this time we did not “hack” anything. We are using good old brute force, enhanced with GPU acceleration, to attack the user’s plain-text master password protecting password managers’ encrypted databases. The four password managers were and still remain secure providing that the user opts for a strong master password. If a truly secure master password is used, it would not be possible to break it within reasonable timeframe.
The Benchmark
Attacks assisted with a top of the line GPU (NVIDIA GeForce GTX 1080 is what we used) return measurable performance. The purpose of our article was not comparing password managers to each other or Microsoft Office encryption. Instead, we wanted to give our forensic customers an idea, a rough estimate of time and resources it would take them to break passwords of certain length.
First, let’s have a look at the wrong scores from the original article:
Below is the new chart with updated password recovery speeds:
So home did we come to the numbers in the first benchmark, and why do they differ from what you see in the second benchmark? The reason lies in our development pipeline. Elcomsoft Distributed Password Recovery supports several hundred data formats, some of which can be protected with adjustable parameters. We started developing support for password manager apps a long time ago. At that time, we saved sample databases for development and testing purposes. Long story short; while we did in fact implement support for the latest versions of all four password managers, our testers still used sample databases from long ago.
So which versions of the password manager apps did we use for our original benchmarks, and which ones do we use now for the new score?
- KeePass 2.36: we measured the same score (120K passwords/s); see note below
- LastPass (Windows Chrome plug-in) 4.1.61; we came to the same score (about 45K p/s). This time, however, we kept attention on the number of hash iterations, which was 5000. Do note that the user can bump this number, slowing down the recovery speed significantly. Rest assured we can attack passwords hashed with any number of iterations, yet the speed of the attack will change proportionally.
- Dashlane 4.8: no surprises, same score (about 130K p/s)
A Word on KeePass
Since KeePass is an open source project, it can be customized. Check out these contributed/unofficial KeePass ports: http://keepass.info/download.html
We received the following comment on KeePass from one of our readers:
It is also worth noting that the number of transformation rounds in KeePass can easily be customized (same for KeePassXC and KeePassX). There is even an option to automatically calibrate a number of rounds which require about 1 second per password attempt on your current machine.
Also the new KDBX4 format wasn’t mentioned at all, which uses Argon2 as key derivation function. Argon2 was specifically designed to make bruteforce attempts really hard and memory consuming (even on GPUs).
Even the official version allows customizing the number of hash iterations. The default value is 6000 iterations on desktops; mobile apps can use the same or lower numbers. In our benchmarks, we used the default value.
In addition to master password, KeePass allows specifying an optional “Key File”, which can be just about any file on the user’s device. This file is then used as an additional extra-long and ultra-secure password; however, if that file is lost or if its content is altered in any way, access to encrypted passwords will be lost forever.
Starting with KeePass 2.35, the database may be stored in the new KBDX4 format. In order to use the new format, the user must manually specify options for database file encryption and key derivation function.
Mobile versions of KeePass as well as unofficial ports are mostly still using the v2 database format (that’s the one we’ve tested). We don’t currently support the new KBDX4 format, but we are ready to add it on request from our registered users. Having said that, we expect seeing significantly lower recovery speeds for the new format since the encryption algorithm is decidedly not GPU friendly.
1Password
The most serious issue we had was with 1Password. The updated score is an order of magnitude slower compared to one we originally measured. Jeffrey Goldberg from AgileBits contacted us and pointed out the problem.
Hello, I am Jeffrey Goldberg from AgileBits, the makers of 1Password.
I am perplexed by your results. In the latest version of 1Password, we use 100,000 rounds of PBKDF2-HMAC-SHA256 in our Key Derivation Function (KDF). Our immediately previous data format (OPVault) used at least (calibrated) 40,000 rounds of PBKDF2-HMAC-SHA512.
Only early versions of our long deprecated Agile Keychain Format, which may have used as few as 10,000 rounds of PBKDF2-HMAC-SHA1 would be make sense for the results that you report. Is that the data format you can recover?
If you are going after the old Agile Keychain Format, then I expect you are getting a 2x speed up from the bug we described in early 2013 (and discovered by the hashcat developers). But we are already deploying the successor of the successor of that data format.
This is where things start getting complicated.
First and foremost, we’ve seen both PBKDF2-HMAC-SHA1 (in old versions) and PBKDF2-HMAC-SHA512 (in new versions of 1Password). We’ve also seen PBKDF2-HMAC-SHA256, which appears in the following cases:
- 1Password10.sqlite (this database comes from the Windows desktop version or 1Password; we don’t support this format yet)
- B5.sqlite (this database is used in macOS for synchronizing with 1Password proprietary cloud service; we don’t support this format either)
In both cases, we’ve seen 100,000 rounds of hashing. We are working on adding support for these two formats to EDPR, expecting to see speeds that are similar to what we currently have (it’s not the hashing algorithm but the number of iterations that matters).
Finally, the profile.js (DropBox sync file) may use 20K to 200K iterations.
1Password supports several storage formats. The iOS app uses OnePassword.sqlite, the desktop version and browser plugins use 1Password10.sqlite (which is completely different from above, and is not currently supported as already noted).
In addition, 1Password supports DropBox and iCloud Drive sync. These cloud services receive a number of individual text files as opposed to a single SQLite database. Breaking the master password only requires a single file named profile.js (or encryptionKeys.js in older versions). Below is a sample:
The algorithm is the same as OPVault (currently PBKDF2-HMAC-SHA512; previously PBKDF2-HMAC-SHA1, like in older Agile Keychain format).
Finally, the number of iterations has always been variable. Moreover, the number of iterations appears to be dynamically calibrated, especially when using mobile version (no idea how it supposed to work for Dropbox sync). We don’t know the reasons and parameters for such calibrations.
The Story of Wrong Benchmarks
Why does 1Password need four different formats and three different algorithms (of which two are current)? We don’t know, but this is the reason why it took us so long to re-run the benchmarks and offer concise explanations. Were our original benchmarks wrong? Not for the latest version of 1Password. Our original benchmarks were measured using one of the four formats and one of the three algorithms supported by 1Password, which happened not to be the combination used in the current version of that password manager.
Long story short, we re-run the benchmark using the latest 1Password 6.8. Now it uses PBKDF2-HMAC-SHA512; iOS version database (extracted from iTunes backup) has 100,000 rounds, while DropBox-synced file opted for 60,000 rounds on our test iPhone 6S (hard to say how much iterations you will get, for example, when syncing older/slower iPhone models, but you can check that yourself, that’s pretty easy).
With these parameters, we came up with 3200 and 6000 passwords per seconds respectively using the same NVIDIA GeForce GTX 1080 board. Much, much better (for customers, I mean).
Our original benchmark had 95,000 passwords per second. This number was measured using a DropBox sync file produced by one of the older versions of 1Password with 10,000 rounds (PBKDF2-HMAC-SHA1). Other files we had (most of them) were using around 25,000 iterations.
This was definitely our error, and we bring our apologies to AgileBits. Rest assured that EDPR supports the latest builds of 1Password (with abovementioned exceptions) regardless of algorithms and the number of iterations. Our benchmarks were an order of magnitude wrong. However, adding a single character to the original password bumps the number of combinations to try by almost two orders of magnitude (considering the choice of all available letters, numbers and special characters).
Jeffrey Goldberg 1password Facebook
Password Managers and Two-Factor Authentication
Some of our readers mentioned two-factor authentication as a roadblock to recovering master passwords. Please note that two-factor authentication is completely irrelevant here as we work with offline databases only.
Jeffrey Goldberg 1password -
Comparing to Microsoft Office?
You may think that we actually compared password managers to Microsoft Office. Of course, we did not. Those are very different tools, even if Excel is in fact used by many for keeping passwords (don’t ask us how we know). We don’t judge the software we break into. What we and our customers care about are the numbers allowing to guesstimate the time required to attack passwords of certain length.
Jeffrey Goldberg 1password Wikipedia
Conclusion
Last but not least. Most modern password managers are very secure. If the entire password database is stored in the vendor’s cloud (e.g. 1Password, LastPass), it’s up to you whether to trust that vendor or not. We did not research the online part at all; our only job was adding support for local databases.
How can you make sure that your passwords are secure with either password manager?
- Use a strong (long and complex) master password
- Never write it down
- Safeguard your data, restrict physical access
- Bump up the number of rounds (hash iterations) if your password manager supports it to further decrease attack speeds
- Make sure you understand that if someone manages to break into your password manager, they will gain access to your every account. In addition, a chain attack may allow them to break in to your other accounts (for which you don’t store passwords with a password manager) by e.g. using single sign-on or recovering a password via email.
41 2 - 43
